
How to encrypt your data with Ecto
If your data is encrypted, even if it’s leaked, no one know what is the data. That’s great. In this post, I’m going to show you how …

If your data is encrypted, even if it’s leaked, no one know what is the data. That’s great. In this post, I’m going to show you how …

Credit: filter image taken from svgrepo.com In web developments, server receives lots of request data from client side. And when working with request …

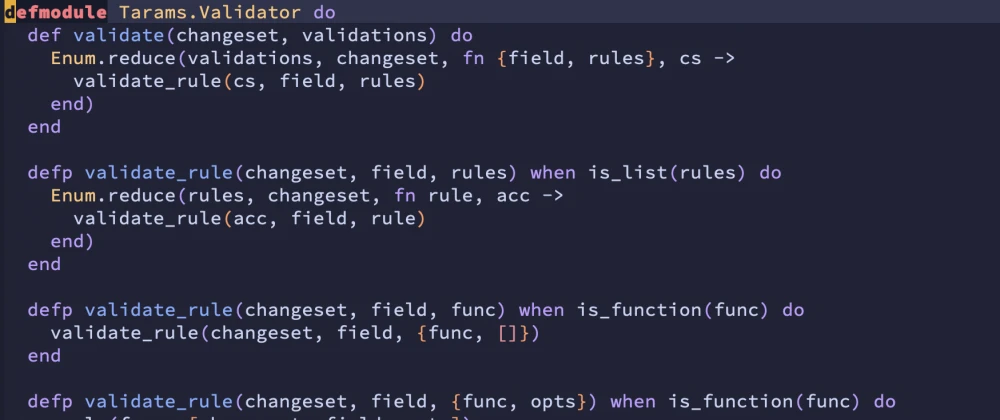
Credit: this icon is from flaticon.com In previous article, I shown you how to implement you own validation module. I you haven’t read it, you …

Validation is a must have part of web application. You have to validate request parameter before processing, you validate data before inserting to …

In my previous article, I introduced my library call JsonView to render json response easier. You can read it here: Render Ecto schema to json with …

When writing API with Phoenix and render json to client, For some fields I want to keep it original value. For some fields, I want to do some …
What is Guard in Elixir In previous post, I explain what is Pattern Matching and how to use it. Elixir pattern matching in a nutshell Pattern matching …